Digital Authentication Introduction

Ciaran Rooney
20 years: technology, cybersecurity & operations
Every time we buy online, post on social media or send a work email, we're using some form of personal identification. But how do the companies know if it's really us doing these things or an imposter? Your password is a good start. In this video, Ciarán Rooney lays the groundwork on digital authentication, from how the concept of passwords came to be and how we measure how good a password is.
Every time we buy online, post on social media or send a work email, we're using some form of personal identification. But how do the companies know if it's really us doing these things or an imposter? Your password is a good start. In this video, Ciarán Rooney lays the groundwork on digital authentication, from how the concept of passwords came to be and how we measure how good a password is.
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.

Digital Authentication Introduction
7 mins 40 secs
Key learning objectives:
Understand basic user authentication
Define a hashing function
Learn how to measure password entropy
Skills:
Overview:
Digital authentication is an integral part of the process of verifying who a person is. It ensures that the user (or the device they are using) matches up to who, or what, they claim to be. Once the user has been verified, they can then be granted access to applications, data, or services. A password is a common tool of authentication. A company should ensure the password is hashed via a one-way cryptographic hash function so that no one can read it. The individual should make sure the password entropy is high - that is, the measurement of the lack of predictability of a password.
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.
What is digital authentication?
Digital authentication is an integral part of the process of verifying who a person is. It ensures that the user (or the device they are using) matches up to who, or what, they claim to be. Once the user has been verified, they can then be granted access to applications, data, or services.
Authentication can also be closely linked to authorisation. Once a system knows who is accessing it, policies can be put in place that dictates what they can and can’t access. Authentication can also be used to raise the alarm when someone is attempting to access something they should not.
How does the ‘hashtag function’ work in relation to passwords?
When a user creates a password and registers it with a service, it will save it alongside the username. The company should ensure the password is hashed via a one-way cryptographic hash function so that no one can read it. Most modern systems will use the Secure Hash Algorithm 2 or SHA 256.
To authenticate, a user simply has to enter their username and password, the service then ‘hashes’ the user’s password before searching for the username and comparing the information with what it has stored. If they’re a match, then the user’s authentication succeeds, and they are granted access.
Why is password entropy important?
Password Entropy is a measurement of the lack of predictability of a password. It is the main measure of the strength of a password or its effectiveness against attacks.
A password's entropy is based on two variables. The first, and the easiest to control, is password length. The second is the range of characters that can be used when creating a password. The character range is expandable by using upper and lower case letters, numbers, punctuation and even symbols.
How does password entropy work?
Password entropy is expressed in terms of bits: A blank password would have zero bits of entropy, while one guessed on the first attempt would have 1 bit of entropy. However, entropy increases exponentially with each additional bit. So while a password with 4 bits of entropy would only require a maximum of 16 attempts to guess it correctly, a password with 40 bits of entropy could require over one quadrillion attempts to guess.
A password's entropy can be calculated by first finding the number of possible passwords that could exist in that password space.
How can the password entropy be calculated?
A password's entropy can be calculated by first finding the number of possible passwords that could exist in that password space. To do this, we raise the number of possible characters in the range used by the password - or R; to the power of the length of the password- or L. For R to the power of L.
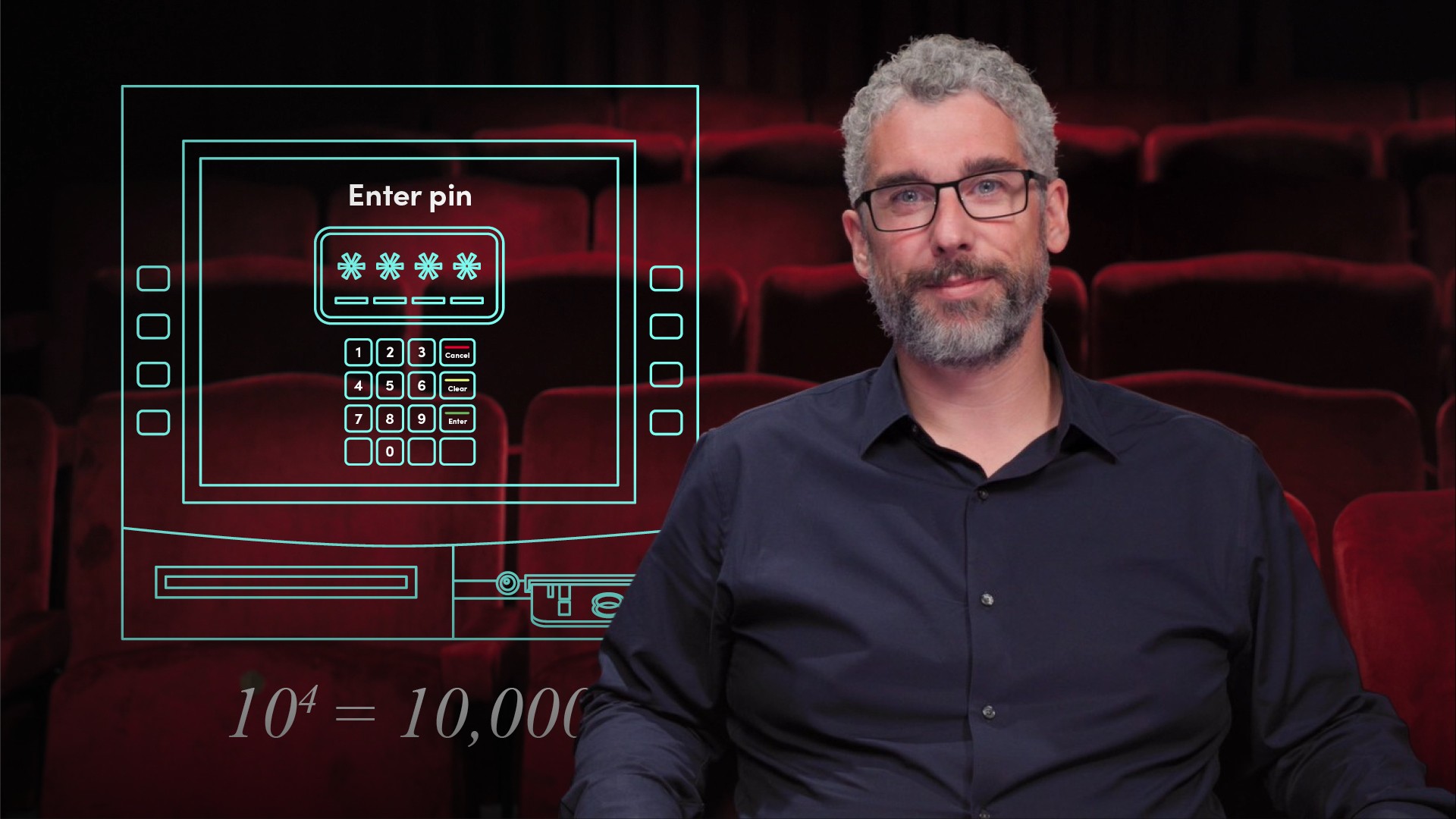
For example, a standard PIN has a character range of the digits 0 to 9, so R = 10 and it is 4 digits long, so L = 4. This gives a password space of 10 to the power of 4 (104) or 10,000.
The next step to calculating password entropy, or E, is to get the base-2 logarithm known as binary log (log base 2 / log2) of the password space.
Password entropy is typically expressed as the formula (E equals the log base 2 of R to the power of L) E = log2(RL).
So for our example, our 4 digit pin would have a password entropy of log2(10,000) or 13.3 bits. To reach our example of a password with 40 bits of entropy, you need to use the typical AlphaNumeric character range of 62 and a password length of 7 or more.
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.

Ciaran Rooney
There are no available Videos from "Ciaran Rooney"